Exploring Kong Ingress Controller (KIC)
Wishing everyone a Happy New Year 2024! In this post, I shift focus from my previous discussion on Kong Gateway to delve into the setup of the Kong Ingress Controller (KIC). Keeping it concise and celebratory for the New Year!
Preparation
Helm serves as a Kubernetes package manager. To install it, execute the following command:
sudo snap install helm --classic
Depending on your configuration, from my K3s master node, I set up my kubeconfig with:
cp /etc/rancher/k3s/k3s.yaml ~/.kube/config
chmod 600 ~/.kube/config
Installing Kong Ingress Controller
Following the Install KIC guide:
wget https://github.com/kubernetes-sigs/gateway-api/releases/download/v1.0.0/standard-install.yaml
# kca is simply an alias for kubectl apply -f
kca standard-install.yaml
Next, create a kong-gatewayclass.yaml:
echo "
---
apiVersion: gateway.networking.k8s.io/v1
kind: GatewayClass
metadata:
name: kong
annotations:
konghq.com/gatewayclass-unmanaged: 'true'
spec:
controllerName: konghq.com/kic-gateway-controller
---
apiVersion: gateway.networking.k8s.io/v1
kind: Gateway
metadata:
name: kong
spec:
gatewayClassName: kong
listeners:
- name: proxy
port: 80
protocol: HTTP
" >> kong-gatewayclass.yaml
kca kong-gatewayclass.yaml
Install Kong via Helm
Add the Kong Helm charts:
helm repo add kong https://charts.konghq.com
helm repo update
Install Kong Ingress Controller and Kong Gateway:
helm install kong kong/ingress -n kong --create-namespace
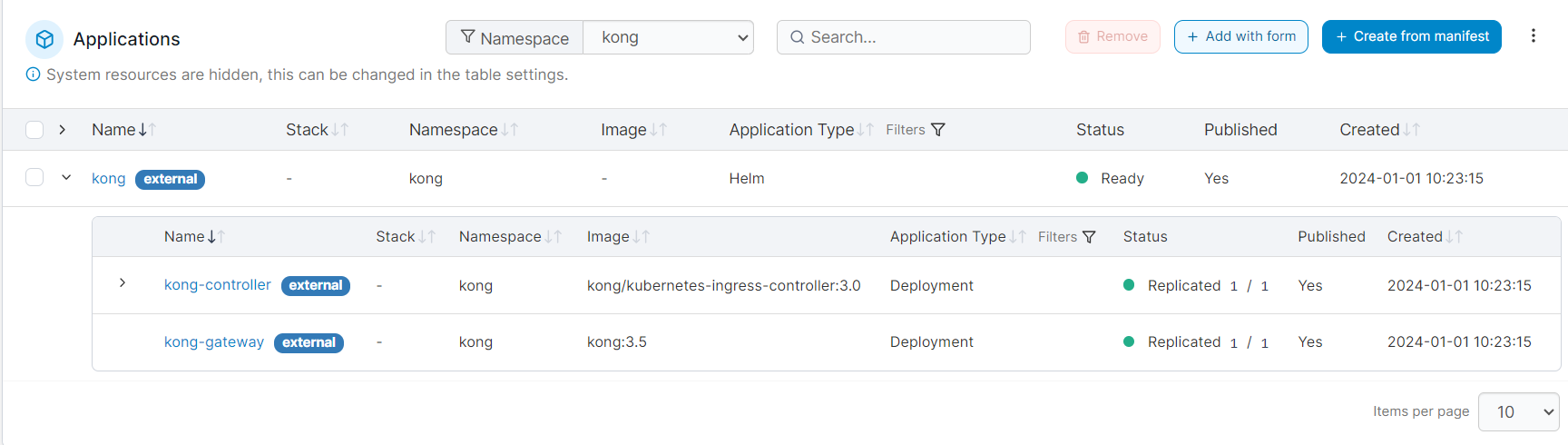
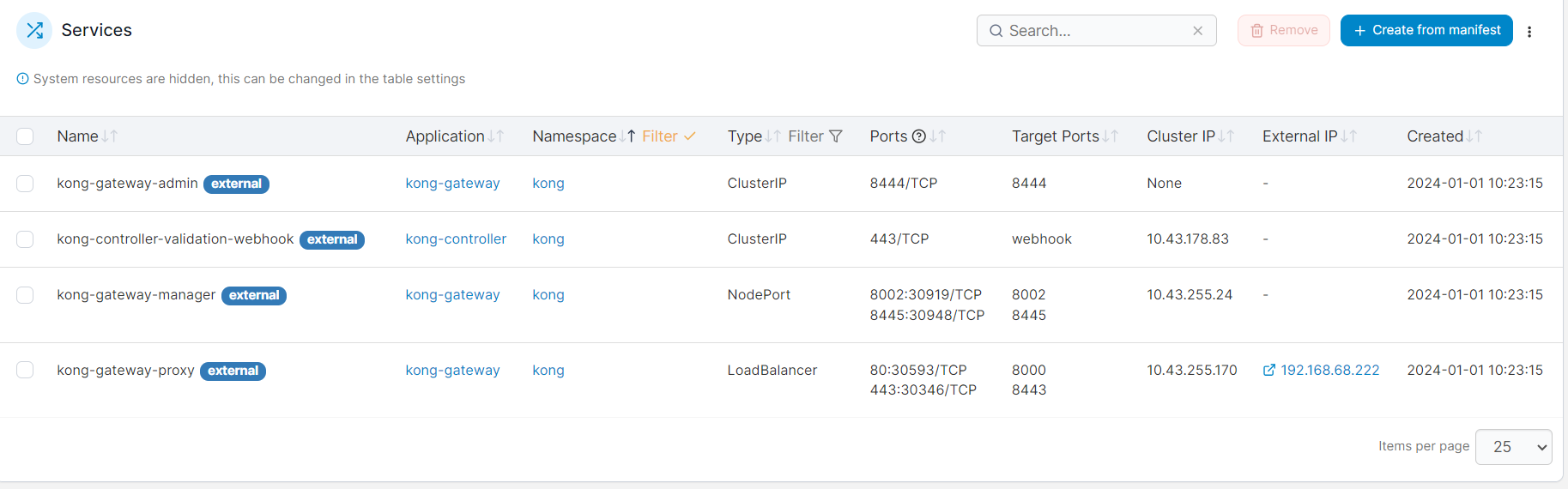
Test connectivity with:
export PROXY_IP=$(kubectl get svc --namespace kong kong-gateway-proxy -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
echo $PROXY_IP
curl -i $PROXY_IP
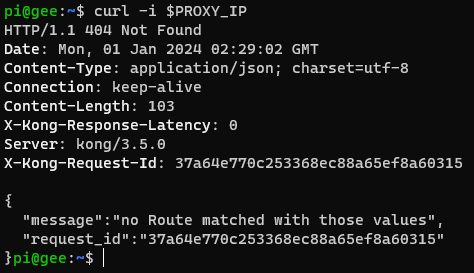
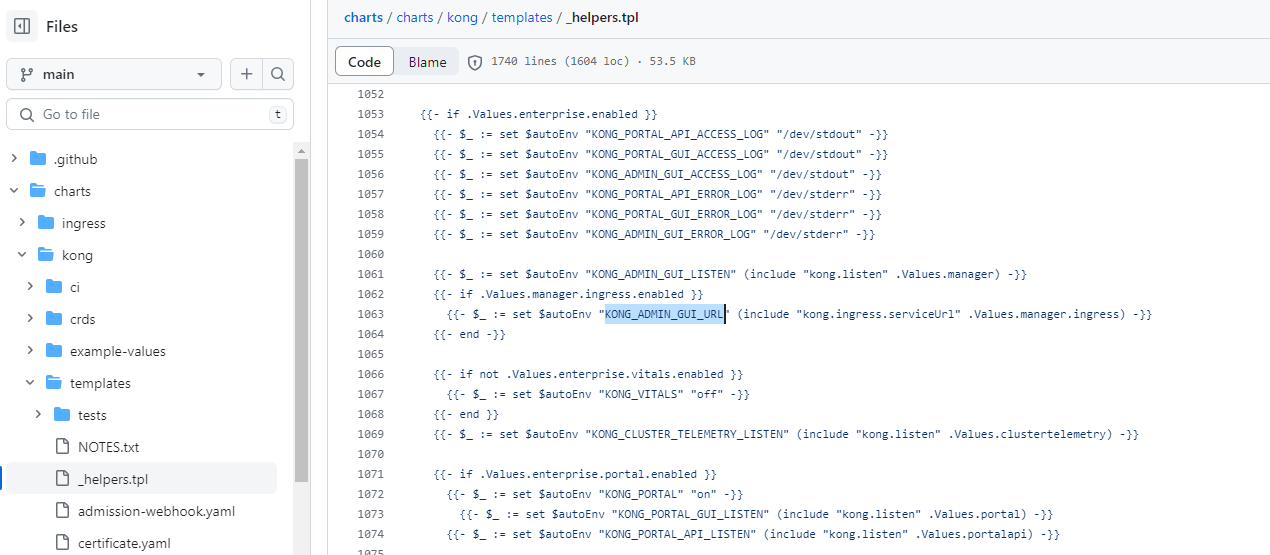
Further investigation into Kong charts reveals that KONG_ADMIN_GUI_URL might be restricted to enterprise editions.
Adding Kong Ingresses
To replicate the previous routing, set up kong-ingress.yaml:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: kong-ingress
namespace: llm
annotations:
konghq.com/strip-path: 'true'
spec:
ingressClassName: kong
rules:
- http:
paths:
- path: /localai
pathType: ImplementationSpecific
backend:
service:
name: localai-server-svc
port:
number: 80
- http:
paths:
- path: /phi2
pathType: ImplementationSpecific
backend:
service:
name: llama-phi2-svc
port:
number: 80
Apply the ingress rules:
kca kong-ingress.yaml
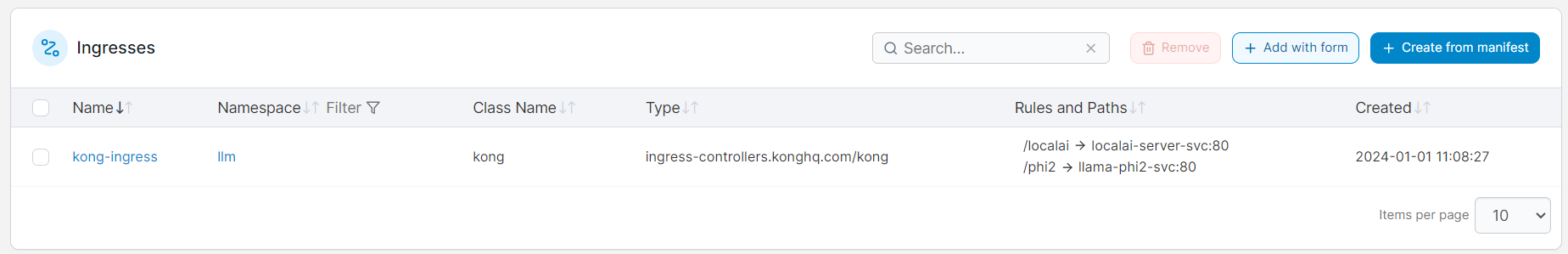
KIC In Action
For testing purposes, I added the following to Windows System32\drivers\etc\hosts file:
192.168.68.222 kic.local
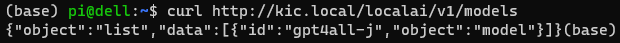
Testing on the localai path from WSL:
curl http://kic.local/localai/v1/models
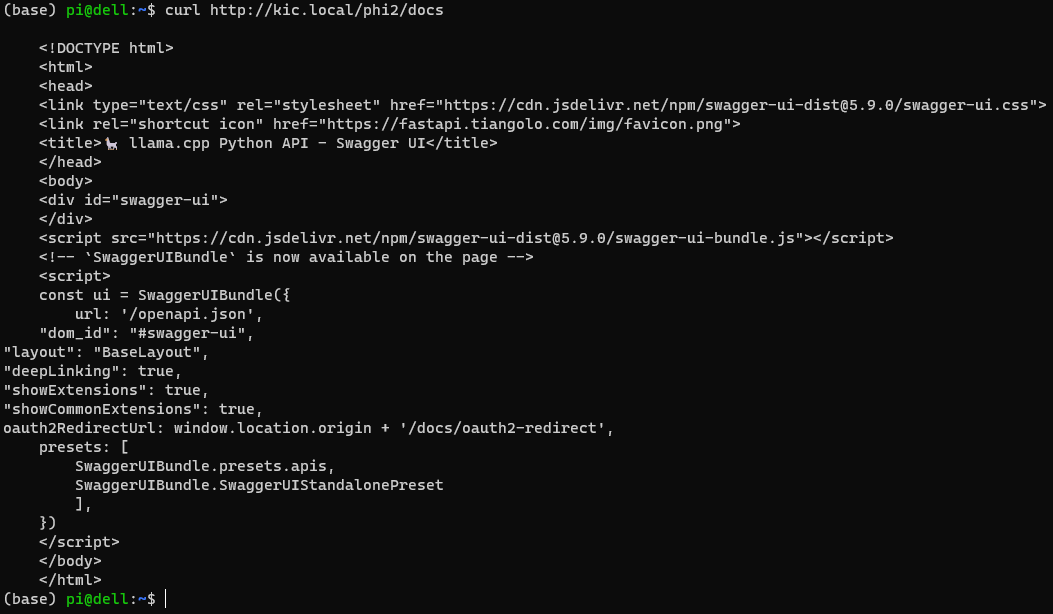
Testing on the phi2 path:
curl http://kic.local/phi2/docs
That concludes the exploration of KIC! Enjoy experimenting! Happy New Year!